Overview
Inbound Internet traffic is mainly determined by search engines. The website rankings in search engines directly affect the marketing effect of a website. This is the context in which Search Engine Optimization (SEO) services have emerged. SEO improves the natural ranking of a website in search engine results based on the ranking rules of different search engines. SEO services are divided into two types. The first type improves the website ranking by legal means such as site optimization, off-site optimization, and content construction. The second type is called blackhat SEO. Blackhat SEO quickly improves the website ranking by using hacker technologies such as spider pools, hidden links, website groups, and server hijacking.
Blackhat SEO generally serves illegal products or websites. Compared with legal SEO, blackhat SEO can improve the website ranking in a short period of time, achieving a fast marketing effect. In addition, the promoted content is not subject to legal restrictions. The main goal of hackers is to make illegal profits and blackhat SEO is an important way to quickly make a profit. A complete black market industry chain has been formed in the underground network sector. Hackers make use of website security vulnerabilities to control websites, implant backdoors, and then sell these backdoors to blackhat SEO operators. Blackhat SEO operators tamper with the website content through technical means such as hidden links or website hijacking to improve the ranking of illegal websites, such as pornography, gambling, or drug-related websites, in search engine results.
The Alibaba Cloud Security Team has recently traced a group of hackers that exploit website vulnerabilities to intrude into and hijack the website homepages for batch SEO promotion. The hacker group controlled a large number of websites and mainly promoted gambling websites, which is very harmful to the Internet industry. Multiple backdoors are often implanted in hijacked websites. The backdoors can be repeatedly used by hackers for profit, resulting in high security risks. The upstream organization under which the hacker group operates owns a large number of IP address resources. To bypass security defense systems, the organization uses thousands of anonymous proxy IP or Dial-up dynamic IP addresses.
The email account dasheng123123@gmail.com is used by the hacker group to register the domain names of all the external links they control. Therefore, the hacker group is named DaSheng.
Distribution of Controlled Websites
According to our long-term tracking, the hacker group controlled and made use of at least 12,700 websites from January to March 2019. Of the top-level domains of websites with hidden links, 72% of domains are “.com”. Many of the affected websites are of non-profit organizations and government institutions, but most are websites of local industry associations and national associations, such as the China XXX Development Institute or China XXX Development Alliance. Making use of the high credibility of industry association and government institution websites, blackhat SEO can quickly improve the ranking of the promoted websites. However, the promotion of pornography, gambling, and drug-related websites by blackhat SEO significantly affects the credibility of these compromised websites. Websites with hidden links have serious security vulnerabilities. If such vulnerabilities are not promptly fixed, major network security events may occur.

Figure 1: Distribution of top-level domains of hijacked websites

Figure 2: Hidden links implanted in the website of a government institution
Analysis of Blackhat SEO Techniques
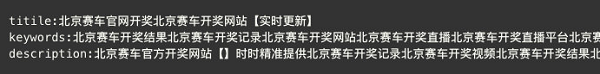
The hacker group inserts the following code in the header of the website homepage through the webshell backdoor. The code modifies the title, keywords, and description of the webpage, and judges whether the browser is a search engine such as Baidu. If the browser is not a search engine, the website title is modified to a legal expression to hide the hidden link.

The modified content is encoded by HTML ASCII and is displayed as common gambling keywords after decoded.
The second JavaScript is obfuscated. After the script is executed, a new JavaScript is generated and linked to the external JavaScript controlled by the hacker group.
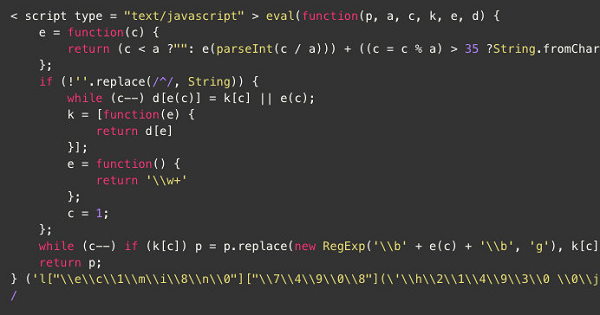
The JavaScript after execution:

The JavaScript automatically pushes the webpage content to the Baidu webmaster platform and 360 webmaster platform. It judges whether the browser is a search engine based on the referrer. If the browser is a search engine, the webpage is redirected to the promoted website.

When you search for the keywords corresponding to hidden links of promoted websites, multiple compromised websites are ranked at the top of the search engine results.

Figure 3: Legal websites tampered with by blackhat SEO
Attack Vectors
The webshell backdoors used by the blackhat SEO group are usually provided by its upstream hacker organizations. Through tracking, the Alibaba Cloud Security Team has discovered the largest supplier of DaSheng. The hacker group has made frequent attacks since January 2019. It mainly makes use of the two Thinkphp5 remote code execution vulnerabilities exposed in 2018 and occasionally uses other web vulnerabilities. Based on the name of the webshell file and main intrusion methods used, we named the hacker group ThinkphpDD.
The DaSheng attack payload downloads malicious code from http://43.255.29.112/php/dd.txt , which is a webshell backdoor. Generally, DaSheng will use the backdoor several days after they successfully intrude a website. To control the website for a long time, DaSheng implants multiple webshell backdoors to different directories of the intruded website. These backdoors are unlikely to be removed by anti-virus software.
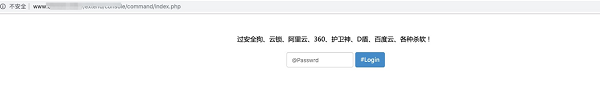

Figure 4: Implanted webshell backdoors
The attack payloads used by ThinkphpDD:

IP Address Infrastructure
Generally, the IP addresses used by attackers can be intercepted by IPS, firewalls, and other security devices based on malicious attack behavior. To bypass security defense systems and reap the highest profits, ThinkphpDD uses a huge number of IP addresses to attack networks. Since January 2019, ThinkphpDD has been using thousands of IP addresses to launch attacks every day. In addition, a few of these IP addresses are reused. More than 100,000 IP addresses have been used by ThinkphpDD. Of the IP addresses used by ThinkphpDD, 89% are from China. According to the proxy IP address threat intelligence of Alibaba Cloud, at least 86% of these IP addresses are anonymous proxy or Dial-up dynamic IP addresses. It is clear that ThinkphpDD has invested heavily in blackhat SEO operations.

Figure 5: Number of attack IP addresses

Figure 6: Number of attacks

Figure 7: Regional distribution of attack IP addresses

Figure 8: Distribution of attack IP addresses
Security Recommendations
1. You must update your services or fix website vulnerabilities in time to avoid intrusion.
2. Inspect the source code of the website and promptly clear backdoors or malicious code implanted in it.
3. We recommend that you use the next-generation Web Application Firewall by Alibaba Cloud to promptly block malicious attacks and set intelligent policies to effectively avoid intrusion.
4. If you have higher custom requirements, you can use Alibaba Cloud Managed Security Service. After you purchase the service, experienced security experts from Alibaba Cloud will provide consultation services and custom solutions to help reinforce your system and avoid intrusion.



